PropelAuth’s SAML SSO support allows your users to connect their organizations to their own identity provider (e.g. Okta, Entra ID, JumpCloud, etc).
As an example, lets say you have a customer “Acme Co”. Acme uses Okta as their identity provider, meaning that all employees at the company have an account with Okta. New employees are onboarded to Okta and exiting employees are removed.
A SAML connection between your product and Acme allows employees at Acme to sign in to your product with their existing work accounts.

PropelAuth’s libraries have a concept of an organization. Users are added to these organizations via invitations or joining by their domain.
One of the best things about our SAML integration is that your code doesn’t need to change at all when you close your first enterprise customer. SAML is an implementation detail of how an organization manages their users within your product. Any code you write that deals with organizations will work, regardless of the method that organization uses to manage its members.
To enable SAML for your PropelAuth project, go to the Signup / Login page in your PropelAuth dashboard.
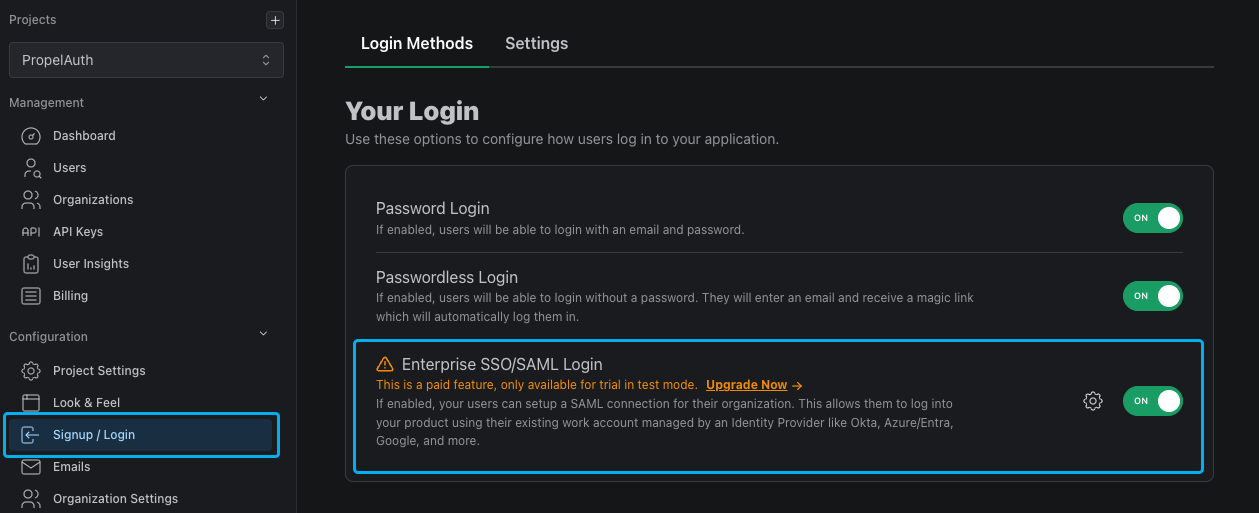
Once you've enabled SAML on the project-level, you can choose which of your organization should have access by going to the Organizations page and select an organization, select Settings, then toggling the "Can this organization set up SAML?" setting.

Alternatively, you can enable SAML for an organization programmatically via the Enable SAML for Org API call.
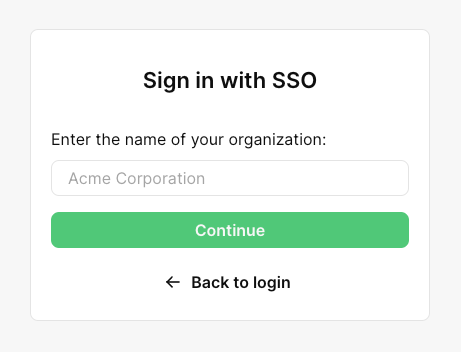
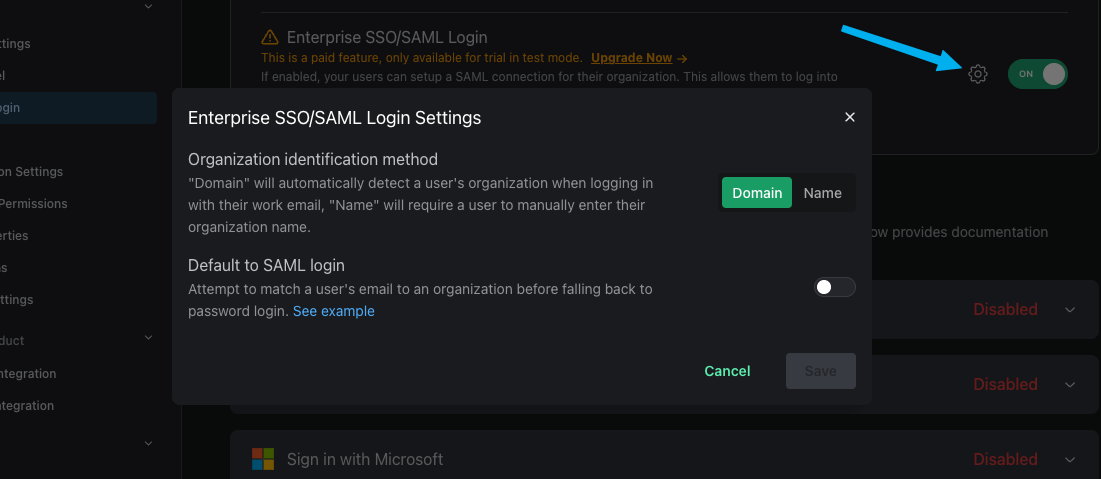
You can also choose how you want to identify which org a user belongs to. When a user signs in and clicks on the Sign in with SSO button, you can either ask for their domain (which will automatically match the domain of their email address with an org domain), or for the name of their org.
You can also choose if you want to set SAML as the default login method. If enabled, PropelAuth will automatically check if an email address belongs to a SAML enabled org. If it does not, it'll fall back to password login.
Once you have enabled SAML for an organization, your users can start setting up SAML with their identity provider. In the Roles and Permissions page in your PropelAuth dashboard, you can choose which roles (Owner, Admin, etc) are able to manage SAML connections.
Any user with the manage a SAML / Enterprise SSO connection for their organization permission can then start the process of connecting to their identity provider. This starts in your user's account page in their organization's settings tab.